Note: Only “Super Admins” have authority to change a company’s password complexity rules. If you are a user that is required to login using multi-factor authentication, please click here to view how to do so.
User login password complexity and multi-factor authentication requirements for ei3 applications can be controlled in two ways. A set of requirements is defined to create a “Password Rule” that applies for company-wide use, and rules can be distinct between the different access levels of users within a Mother Company in the Customer Portal. All rules may only be created and managed by Remote Service super-admin users. Please note that password requirements and multi-factor authentication care configured inside Remote Service and Customer Portal.
A Remote Service super-admin user would first create one default rule for all users for their own company. This default rule will also apply to all the customer Mother Companies in the Customer Portal that were set up by that parent Remote Service company, unless a separate rule set is created for those companies. Such separate rules can also be segregated by user access level (non-admin, location admin, division admin, company admin).
Accordingly, additional, distinct rules may be created for individual customer Mother Companies. Such a rule would apply to the relevant Customer Portal users of that Mother Company.
- Creating or Editing Password Rules
- Password Complexity Composition Rules
- Password Complexity Security Setting Rules
- Multi Factor Authentication
Creating or Editing Password Rules
Log into Remote Service, go to Admin and then click on the Password Rules menu item. This will take you to the following page:
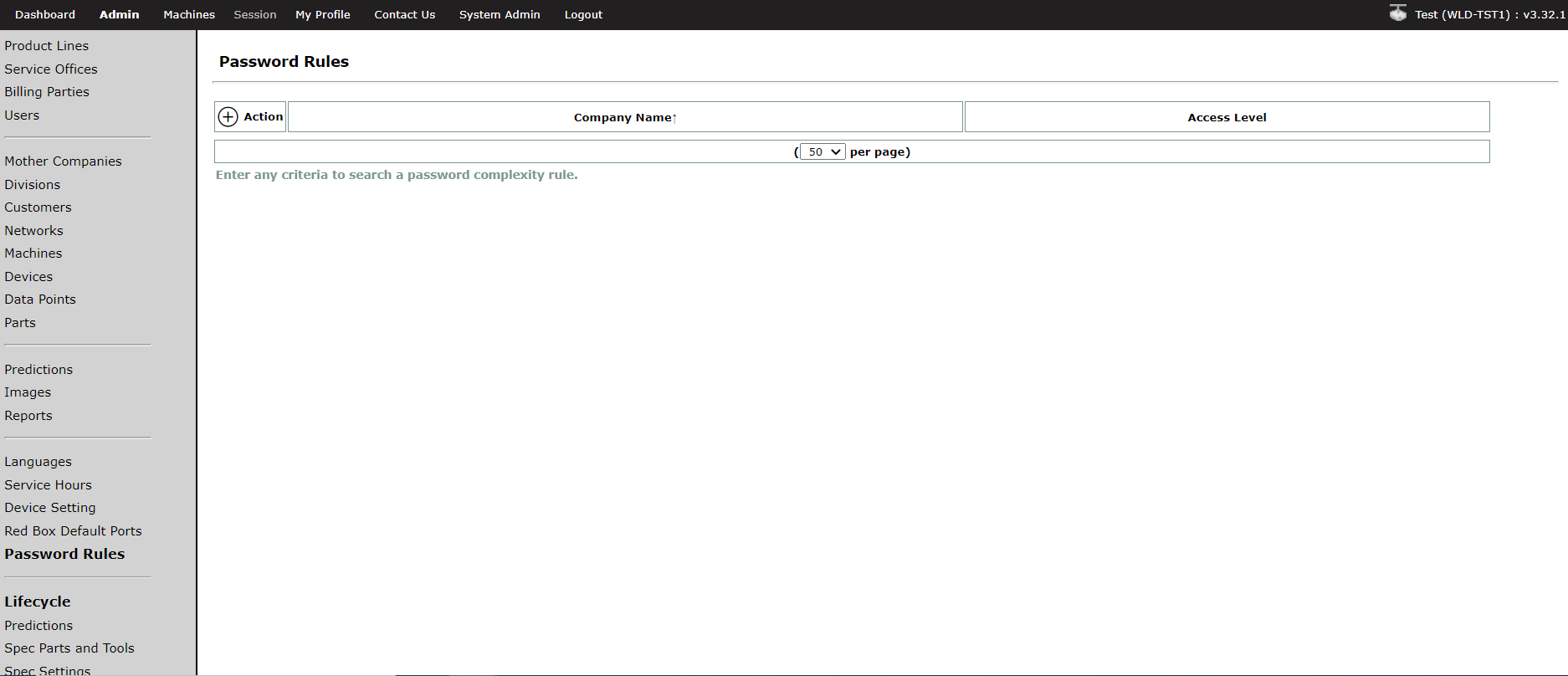
![]()
To create a new password rule, click on the next to the Action column. The super admin should first create a default password rule for their own company and all its customer companies in the associated Customer Portal. Then if different requirements are desired for a specific mother company, a different rule can be created for just that mother company. A rule for a specific mother company will only apply as the unique default for all users in that company. In addition, password rules can be created for the different user access levels at the customer mother company. In summary, the super admin can create different password rules for different companies or different user access levels.
When creating a new password rule, the rule is defaulted to affect all users at all access levels as shown in the figure below. In this example below, “ei3 Corporation” is the Remote Service OEM company.
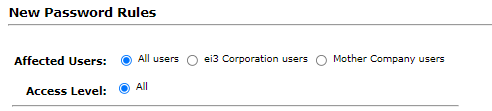
To create a Password Rule for a particular Mother Company, the super-admin can select the Mother Company users option and then select the specific the company from the drop-down list. Then they must select which access level(s) within the Mother Company users to which they would like this rule to apply.
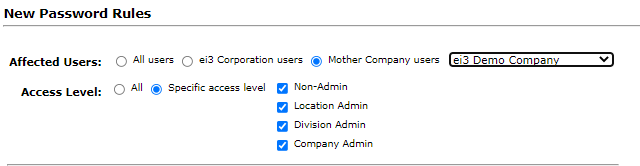
Password Complexity Composition Limits
The following composition limits apply to all password rules:
|
Composition Requirements |
Number of Characters |
|
Length |
Between 8 and 128 |
|
Minimum Alphabetical Characters |
Between 1 and 10 |
|
Minimum Numeric Characters |
Between 1 and 10 |
|
Minimum Special Characters |
Between 1 and 10 |
|
Minimum Uppercase Characters |
Between 1 and 10 |
|
Minimum Lowercase Characters |
Between 1 and 10 |
A number of characters must be defined within the limits for each composition requirement. The super admin can also enable the rejection of commonly used words as passwords and user-derived words as passwords by selecting the relevant boxes to enable those settings.
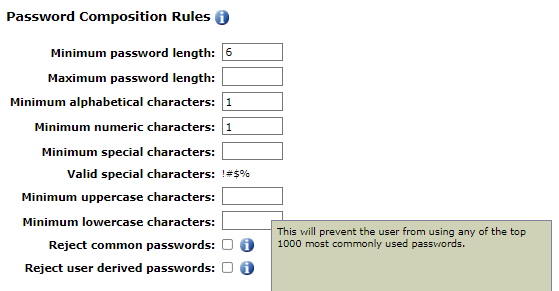
The Reject common passwords will not allow a user to use any of the top 1000 most common passwords, while the Reject user derived passwords will not allow the users password to include their username regardless of capitalization.
Password Security Setting Limits
The following security setting limits apply to all password rules:
|
Security Setting Requirements |
Number of days / tries |
|
Maximum Password Life |
Between 1 and 3650 days |
|
Password Change Reminder |
Between 1 and 365 days |
|
Failed Login Attempts |
Between 1 and 10 times |
|
Password History Length |
Between 1 and 10 passwords |
|
Lock Inactive Users After |
Between 1 and 3650 |
The Maximum Password Life (days), Password Change Reminder (days) and Password Length History sections also have the info ![]() icon to explain what that section means.
icon to explain what that section means.
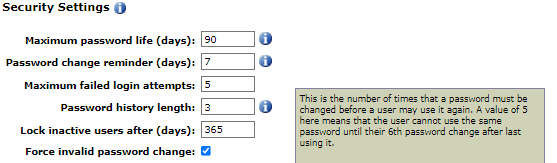
The Maximum Password Life (days) is the maximum number of days since the user last changed their password before the user is forced to change their password.
The Password Change Reminder shows a reminder message to the user of how many days before the password will expire and they will be forced to change their password. In this case, the reminder message will appear every day starting 7 days before the password expires (day 83 of the 90 day maximum password life).
The Password History Length is the number of times a password must be subsequently changed before an old password can be reused. In this case, after changing the password 3 times since a particular password was last used, the user can use that same particular password again.
At the bottom of the Security Settings section there is a checkbox to Force invalid password change. When this is checked, it will force users to change their password if their current password no longer meets the password rules, regardless of whether their password life has expired.
Multi Factor Authentication
In this section, the super admin can choose whether they want to enable two-factor authentication. Clicking the checkbox will require two-factor authentication for all users to which the Password Rule applies. For increased user convenience and slightly less security, the Allow user to remember their device check box can also be checked, which will allow users to skip the two-factor authentication process when logging in from a familiar computer.
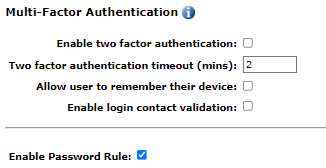
A timeout is required when enabling the two-factor authentication. Once the email or text with the code is sent to the user, the value of the timeout provides that quantity of minutes within which the user must use that code. In this case, the user has 2 minutes before that code expires and can no longer be used for login.
Selection of the Enable login contact validation checkbox will ensure that users have a valid email address and phone number in their profile. If they do not, they will be redirected to update that information in their profile prior to logging in.
Once all settings of a Password Rule are complete, the Password Rule must be enabled by checking the Enable Password Rule box at the end. The super admin can enable or disable it at any time, and changes will take effect immediately upon saving it.

