Two-Factor Authentication (2FA) is a form of security that requires two forms of identification to access the application. These two forms must comprise something the user knows, and something the user possesses. In ei3 it adds an extra step to the log-in process, which sends a unique and random code to the user’s phone or email. ei3 highly recommends using this capability, as adding this extra step to the log-in process will make user accounts more secure.
2-Step Verification Process
When 2FA is enabled for a user, the user must have a valid email address and phone number in their ei3 user account profile. That way the user would have two methods available for verifying their identification when logging into the system. As soon as the user logs in with their username and password, which is the first step in the verification process, the user is then asked to select a method for receiving a code for the second step of the verification process.
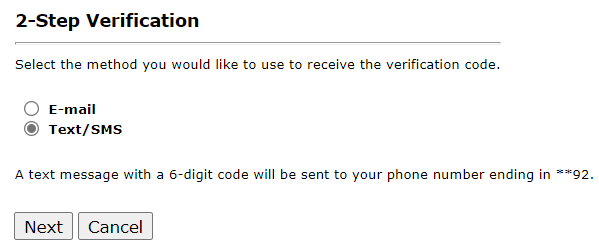
Once a method is selected and the user clicks on Next, the user has a specific number of minutes as defined by the super-admin system administrator, to enter the code they received by either text or email.
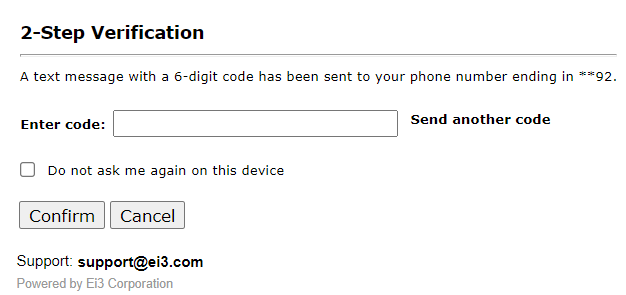
In case the code is not received, the user can click on Send another code to receive a new code, or the user can click on cancel and enter the username and password and select another method of verification. Once the code has been entered, click on Confirm to complete the two-factor authentication, and the user can now access ei3.
Note: Two-Factor authentication settings need to be defined and enabled by the relevant ei3 super-admin user.
The user can also choose to remember the device from which they are logging in, to avoid having to go through the two-factor authentication process every time they log in on the same computer. This can be done by click on the Do not ask me again on this device box as shown below:
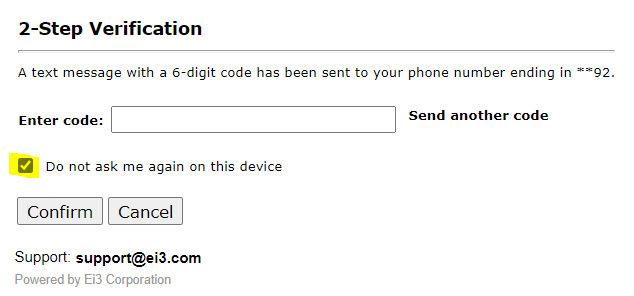
Users should not check this box unless they are certain that their device is secure and is not used by anyone else.
How do I do Multi-Factor Authentication Without a Cellphone or Email?
In certain cases, such as with operators working in a restricted factory shop floor, some ei3 users may not be allowed to have access to a cellphone or email while at work. In such environments where this occurs, we recommend the following:
- A supervisor or other employee who has or can temporarily gain access to their email and phone in such an environment can enter those into the user ID of the person who needs access to ei3 at a specific computer terminal. The supervisor will then need to be present to set up the initial MFA login and use the “Remember my device” feature for the user to login in after that time, using the same computer and browser.
- This will need to be repeated each time the password expires and must be reset.
© 2024 ei3 Corporation. Content of this web page is proprietary to ei3 Corporation.

